-
[1.14.3] Client-Server handshake goes wrong
Got it working without help, I just pass the handshake packet which comes from the client to the server. But I'm still wondering how the 1.14 handshake works...
-
[1.14.3] Client-Server handshake goes wrong
Alright thanks for your great help. I'll then just dig down forge's code... Why doing things easy if you can do it complicated...
-
[1.14.3] Client-Server handshake goes wrong
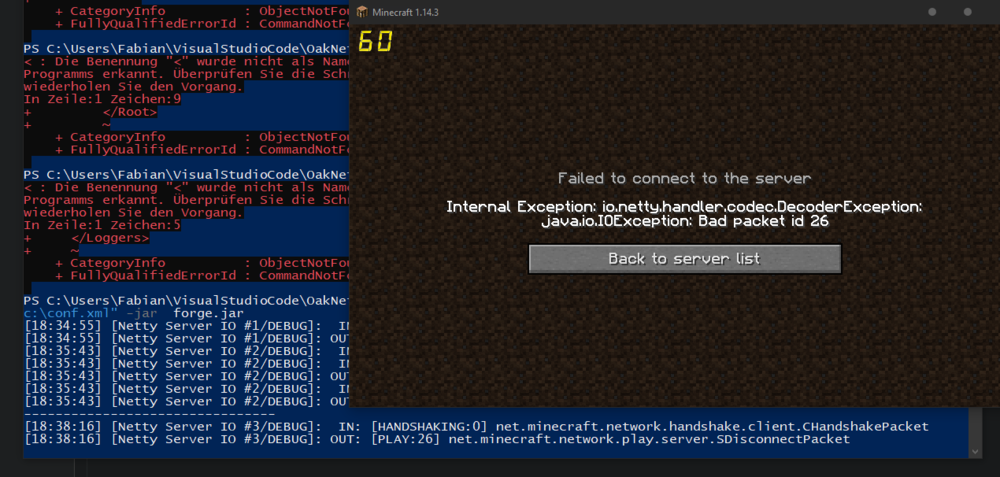
My code is already working. I like to have a simple solution for the user. Hamachi is to much efford for some users. In 1.12.2 forge server are working. Vanilla servers are also working. They're also working in newer minecraft versions. Only the forge server makes problems...
-
[1.14.3] Client-Server handshake goes wrong
I'm working on my mod: https://www.curseforge.com/minecraft/mc-mods/oaknetlink I need to fake the handshake to let the server accept my bot which carries the packets to other "real" clients
-
[1.14.3] Client-Server handshake goes wrong
Hello fellow modders, What does the forge server expect for handshaking? If I try to send the normal handshake with the adress: "localhost\0FML\0", which worked in 1.12.2, but now it just responds with the play packet 26: "SDisconnectPacket". This results in the client throwing the error: Internal Exception: io.netty.handler.codec.DecoderException: java.IOException: BadPacket id 26. Perhaps the handshake was changed in the forge rewrite? My code for the handshake: byte[] protocolVersionBytes = McPacketOutEncoder.encodeVarInt(490); byte[] serverAdressBytes = McPacketOutEncoder.encodeString("localhost\0FML\0"); short port = 25565; byte[] portBytes = new byte[2]; portBytes[0] = (byte) (port & 0b0000000011111111); portBytes[1] = (byte) ((port & 0b1111111100000000) >>> 8); byte[] nextStateBytes = McPacketOutEncoder.encodeVarInt(2); byte[] newPacketData = new byte[protocolVersionBytes.length + serverAdressBytes.length + 2 + nextStateBytes.length]; System.arraycopy(protocolVersionBytes, 0, newPacketData, 0, protocolVersionBytes.length); System.arraycopy(serverAdressBytes, 0, newPacketData, protocolVersionBytes.length, serverAdressBytes.length); newPacketData[0 + protocolVersionBytes.length + serverAdressBytes.length] = portBytes[0]; newPacketData[1 + protocolVersionBytes.length + serverAdressBytes.length] = portBytes[1]; System.arraycopy(nextStateBytes, 0, newPacketData, protocolVersionBytes.length + serverAdressBytes.length + 2, nextStateBytes.length); byte[] packetIDBytes = McPacketOutEncoder.encodeVarInt(0); int packetLength = packetIDBytes.length + newPacketData.length; byte[] packetLengthBytes = McPacketOutEncoder.encodeVarInt(packetLength); byte[] handShakePacket = new byte[packetLength + packetLengthBytes.length]; System.arraycopy(packetLengthBytes, 0, handShakePacket, 0, packetLengthBytes.length); System.arraycopy(packetIDBytes, 0, handShakePacket, packetLengthBytes.length, packetIDBytes.length); System.arraycopy(newPacketData, 0, handShakePacket, packetLengthBytes.length + packetIDBytes.length, newPacketData.length); sendPacketBack(handShakePacket);
IPS spam blocked by CleanTalk.